CyanogenMod, an alternative open-source firmware distribution for Android smartphones and tablets, has been recording the swipe gestures used to unlock the devices, a developer involved in the open-source project said. The issue has been corrected in an update.
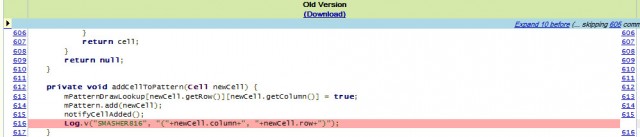
Gabriel Castro noticed an extra line of code that appears to have been added in August, when CyanogenMod was updated to make the grid size for screen locks configurable rather than fixed. In the process, the line was added, causing the unlock pattern to be recorded in a log file stored on the device.
"I'm really surprised nobody caught this," Castro wrote in comments accompanying a fix. An alternative to removing the line is adding a character to the code so it's treated as a comment and isn't executed. Either approach can be done "without breaking anything," he added.
The undocumented screen-lock logging isn't as serious for most users as many reported vulnerabilities are. To exploit the weakness, an attacker would first have to gain access to a device, or possibly a device backup stored on a hard drive. That makes it hard for an attacker to exploit the weakness on a large number of devices.
Still, the logging behavior could be of use in targeted attacks. Further, security experts have long cautioned against the storing of passwords, personal identification numbers, and other forms of passcodes in plaintext or even in an encrypted format that can be reversed. Logging the pattern required to unlock a phone is something that's unnecessary and can only diminish security.
As many as 2.5 million phones have installed CyanogenMod, which offers easier updating and is therefore viewed by some users as a more secure alternative to official carrier releases that often can't be upgraded regularly or at all. There's no benefit to having unlock patterns logged, so it makes sense to install the patch.
2012 ncaa bracket john carlson greg smith catamount mike dantoni bulls heat goldman sachs
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.